Chapter 4
Searching for an opportunity
A question of strategy
The last chapter illustrated by way of simple financial calculations that large sums of money thrown at the problem of finding an e-business solution in the chaotic environment of the Internet is largely wasted. From an investor's view point this is not only off putting, it can be a convincing argument for them not to invest at all.
However, the advantages of finding and exploiting the enormous potential of the digital communication environment are only too obvious. This presents a paradox: it is not profitable to invest in e-businesses, but, there are numerous opportunities for making a profit. The resolution of this paradox is to think in terms of strategies.
Most people, when asked to name a game of strategy, will answer, "Chess". This fits in nicely with the conception of strategy as it was envisaged in the Industrial Age. It is a game where there are many alternative options, each of which can be countered by an opponent and the way to win is to be better than your opponent at seeing ahead. Working out all the possible moves that are available to both players over a sequence of moves is the key to a winning strategy.
Computer programs designed to play chess use this strategy to win against human opponents. They can rapidly analyse the alternatives and consequences of millions of possible moves and thus keep ahead of a human who has far less ability to deal with so many possibilities.
The only reason why a computer can be programmed to beat a human at chess is because the environment of the chess game is very unique. All the information that is needed to plan ahead is available on the board. Apart from competitive moves, all possibilities are known and, by assuming an opponent plays logically, even these competitor moves are predictable.
In the industrial world of the twentieth century, business strategies could be similar to chess playing strategies. With the aid of statistics, probability and market research, business strategists could have a pretty accurate idea of what the future holds and be able to make optimum choices from a range of possibilities.
In the chaotic environment of the Information Age, the future is not predictable. Using conventional Industrial Age business strategies is much like a computer program having to play chess when it is only allowed to see the positions of a few of the pieces on the board. In such a situation, a conventional, chess type strategy is totally useless.
Human brains have evolved to deal with uncertain and incomplete information. Unlike chess playing computer programs, humans don't examine every possible alternative way the future can unfold. Unconsciously, the human brain ignores most possibilities and gambles on just a few of the most likely scenarios. This strategy relies upon an ability to respond rapidly if things go wrong because logical reasoning cannot be used to anticipate and avoid unfavourable future events.
Philip Johnson-Laird, a psychology professor at Princeton University has been working for over a decade to prove that humans do not naturally use logical reasoning and rational rules to make decisions. He concedes that humans are capable of using this method of deduction to think problems through and make strategic decisions, but, he claims that this is only a relatively recent evolutionary feature brought about by the conditions prevalent in an ordered society.
Johnson-Laid believes it is more natural for humans to carry a rough model in their heads rather than pursuing every possibility through to its logical conclusion. To explain this, he devised a simple little puzzle:
Only one of these statements is true:
1) There is a king in the hand, or an ace, or both.
2) There is a queen in the hand, or an ace, or both.
3) There is a jack in the hand, or an ace, or both.
Is it possible that there is an ace in the hand?
Most humans would answer, "Yes", but, a computer logically programmed to solve this puzzle would give the correct answer and say, "No".
Johnson-Laird explains that humans get the wrong answer because they have a limited space in what is called "working memory", the area of the brain that deals with logical reasoning. When this memory is overloaded with too many possibilities, it leaves out part of the information: sometimes resulting in an inaccurate mental model.
The brain decides what to leave out by ignoring information that throws up ambiguity. For example, being told that the statement — "Oliver is clever and Elliot is stupid" — is false, throws up many alternative possibilities. The brain tends to ignore this kind of statement because the processing involved in examining all the possible meanings uses up too much working memory.
In the puzzle above, the brain unconsciously recognises the complexity involved in considering falsities, so will ignore the fact that only one of the statements can be true. A more pedantic reasoning process would observe that if there is an ace in the hand the first two statements must be true and as it was specifically stated that only one of the statements was true then it isn't possible for there to be an ace in the hand.
The observations of Johnson-Laird, based on testing many variations of this puzzle on students, seem to indicate that the human brain has evolved to sacrifice accuracy for the sake of expediency. When quick decisions have to be made there isn't time to consider the consequence of every action. In this process, falsity considerations are often ignored. This throws some light on the strategy preferred by evolution. Our brains would have evolved greater processing power if this had been essential. Instead, the survival of the most successful resulted in brain mechanisms that went for expediency.
It is this, more natural strategy, that is characteristic of entrepreneurs working in a new and changing environment. If they stopped to examine every possible consequence of their actions, they'd never progress. Instead, they ignore uncertainties and unknowns and make initiatives based upon conceptual models that do not contain specific detail.
In one sense, the entrepreneur is in the same position as an investor: being unable to avoid mistakes and errors of judgement. But, by using an appropriate strategy, the mistakes and errors can result in little cost that will be more than compensated by gains. The way an entrepreneur does this is to:
1) Work with non detailed conceptual models
2) Maintain low overheads
3) Create multiple opportunities
4) Establish a variety of strategic contacts
5) Not get locked into single fixed ideas
6) Think in terms of reconfigurable components that can be used in a variety of different situations
In this way, an entrepreneur can remain flexible enough to weave around any setbacks and misjudgements that would bring more carefully planned projects to a jarring halt.
To illustrate how reasoning and logical analysis can handicap an entrepreneur, we might consider two of the most important areas of business: ideas and trust. Ideas abound in a fertile entrepreneurial mind, but, if every idea was thoroughly thought through, to examine every possible problem and consequence, none of the ideas would ever be put into practice. Similarly with trust. If an entrepreneur had to check up on everyone they had dealings with before forming an alliance or association their progress would be too slow to be able to respond quickly to opportunities.
Ideas and trust
The first chapter described the concept of the virtual cafe, which is a conceptual device for communicating and collaborating with a variety of contacts. One of the collaborators in the cafe, commented:
A question about how the e-business ideas will develop. I'm sure every collaborator could come up with an idea right now, but if starting out with one good idea is not the way forward, will fifty ideas be better? Also, (and this is very traditional business in thought) are we comfortable enough to offer ideas at this point? I mean, has a relationship of mutual trust been created yet?
Katherin Ekstrom
These two points have been covered in the first two books in this trilogy. Firstly, starting with specific business ideas is very limiting. Secondly, we have to assume that we can't trust anyone else. Let's recap here:
Initial ideas
The first book in the trilogy "The Entrepreneurial Web" proposed starting any e-business venture with a green frog. This green frog is the business idea and the business plan. Of course, this represents something ludicrous. How can a serious e-business be started with nothing more in mind than a green frog?
The point is that it is better than having a fixed idea or a business plan because you have no preconceived notions. An e-business can emerge more easily out of a green frog because you are forced to start from first principles, allowing ideas and opportunities to emerge without the danger of being sidelined into dead ends or handicapped by knowledge gaps.
Starting with an e-business idea and a plan is much like having a great design for a house and then trying to build it on quick sands. The sensible place to start is to look for solid ground and then build firm foundations. It is only then that the design of the house becomes relevant.
The idea of starting literally with a green frog is a way of being able to avoid a stereotyped way of thinking. Following what everyone else is doing or thinking either gives you unnecessary competitive pressure or sees you following the lemmings over the cliff. Stereotyped thinking is not the way to find a breakthrough into a novel way of doing business.
Trust
This was dealt with in the second book of this trilogy "The Ultimate Game of Strategy". The conventional notion of trust, as it is understood in the world of bricks and mortar, has no relevance in e-business. In its place is the notion of "playing the game intelligently". This means that although you might not have any basis for trusting somebody in the conventional sense, you may be able to trust them to act rationally in their own best interests.
By assuming that people are going to act selfishly, you know where you stand. You can predict what actions they should take to act in their own best interests and in this sense they will act reliably. This is much better than not being sure whether or not you can trust somebody.
This different form of trust assumes everyone will renege on a deal, steal a march, take your ideas for themselves, copy what you are doing, etc. if it is beneficial for them to do so. If this is assumed to be a legitimate way for others to play the game then the best strategy is to so structure your e-business dealings that it would not be in their best interests to do such things.
A little trick I learned from a shrewd old Jewish milliner was to give people a chance to cheat early in a relationship. If they cheated her, when she gave them the opportunity to do so, she would consider it a small premium to pay for a little insight into their character. It paid her to find out early in a relationship because it might save her from being at a greater risk of loss later, when dealings might be more substantial. It didn't stop her doing business with the cheaters though, she just dealt with them differently.
The question of trust in e-business is a calculated risk based upon the perceived relative values of the immediate gain of the cheat balanced against the loss of potential gains they might have by not cheating.
In the particular case of the collaborators involved in this book, the gains and losses of the fifty people have to be individually assessed on the basis of whether it will be more profitable for them to leave the group and run by themselves with any emergent opportunity, or, whether it will be more profitable for them to develop an emerging opportunity within the group.
This is another reason why ideas are not appropriate at an early stage in creating an e-business; people can steal or copy ideas, especially if the ideas are any good. Better for ideas to emerge after valuable relationships have been established then the cost of running off with an idea has to be balanced against the cost of losing the relationship. Ideas are cheap and plentiful, but, relationships cost time and effort to establish.
The thought that you can work without ideas and without trust or loyalty will seem utterly bizarre to most people. The trick is to realise that the e-business environment is about connectiveness and dynamic systems. Products, services and businesses are not isolated separate entities. They are all part of a whole where each part is dependent upon many other parts.
The individual, the isolationist, is at an extreme disadvantage because in any dynamic system the whole is worth much more than the sum of the parts. In a relatively simple world, people can offer a product or service which is complete in itself. They can be self contained and self sufficient. In a highly complex, interconnected environment such as the Internet, business or personal contributions are mostly only a very small component of a much larger and often incomprehensible higher order of natural organisation.
The benefits of being included within a system of many others is likely to be far greater than striking out alone. This knowledge provides a good reason for collaborators to remain with a group rather than cutting and running. Ideas are plentiful, but, links into a system of people are much harder to acquire.
It also give a clue as to what we should start looking for in an e-business opportunity. We should be searching to find or create a system to join. As a foundation, this would be far more valuable than simply a novel idea.
What are we looking for?
In 1999, Bill Gates gave an in depth interview for the first time to a UK television station. For many people in the UK computer industry, this broadcast was eagerly awaited with great expectations. Here was the most successful exploiter of computer technology in the world, setting out his views. What gems of wisdom would be forthcoming? What vital clues might he reveal that would point to a new direction forward.
The day following the broadcast there were discussions on most of the UK e-mail discussion forums that I belonged to, analysing what he had said in the interview. The general consensus was that he'd disclosed no useful information at all. The whole interview had seemed to most people to be banal and completely lacking in any useful information or knowledge.
I was totally amazed by this reaction because it had seemed to me that Bill Gates had summed up, in a nutshell, his entire strategy for success. It was so simple, so obvious, that most people had missed the significance. They had been looking for something clever, something that only a super brain could have thought of. In fact, it wasn't anything like this at all: it was just plain common sense.
Bill Gates had explained to the interviewer that Microsoft had created an environment. Then, in trying to make full use of that environment, they had designed tools for themselves. Other people wanting to explore and exploit this same environment would also have use of these tools. These people became customers.
The important clue this revealed was that Bill Gates saw his success in terms of pioneering and finding out for himself what could be achieved rather than trying to work out what other people wanted. It was a reasonable assumption that the tools he found necessary to develop for himself would also be needed by others.
This then is another pointer to a way of discovering an e-business opportunity. We simply explore an environment. The tools or methods we need to create along the way may lead to a revenue generating situation. As Bill Gates discovered, it is inefficient for people to reinvent the wheel; if somebody has already discovered some time saving method or application, others will be willing to pay a small price to acquire that same advantage.
As a metaphor, we might think of America in the seventeenth and eighteenth century. Settlers arriving from Europe would find a land of potentially unlimited opportunity. But, their first problem would have been where to travel in order to find the best place to settle. They would need maps, guides, transportation, tools and provisions. The earliest pioneers, the explorers, would have been in the best position to know what was wanted and be able to provide these services, thus they would have been able to profit as a result of their pioneering experiences.
The first settlers arriving in America wouldn't have been sensible to have set off alone. They would have traveled with many others. In this way, they could get help from each other with any problems that came along. They would each have needed a variety of different services and these could only come from within a community.
When the settlers found an appropriate place to settle, they would have needed to settle as a community, each taking up a necessary niche to cater for a particular aspect of the community's needs. In this way it can be visualised that it is the community that is the key to everyone's success and everyone contributes to and feeds off of its strength. Yet, at the same time, everyone can be independent and free to act on their own initiative.
The Internet is much like the unexplored Americas. We need maps, guides and tools. We will have great difficulty in going alone so we need to look for traveling companions who can provide assistance or specialty help as it is needed. In short, everyone needs to be part of a collaborative community. Thus, this should be the first consideration when starting to look for an e-business opportunity.
The self centred virtual community
Communities are usually thought of as being based upon trust and loyalties. But, these are not relevant in an e-business environment because it has to be assumed that everyone will be looking out only for themselves and will help others only if it is in their interest to do so.
What kind of community can be created on this basis? To solve for this problem we have to tear up our idea of what a community is in the world of bricks and mortar and create a more practical version for the world of e-business.
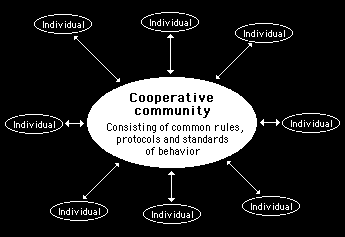
The conventional idea of a community is that it provides an environment where people are tied together through a common set of rules and protocols. These rules and protocols override personal idiosyncrasies and there is great pressure on all individuals to obey implicit or explicit common codes of conduct. This is illustrated in figure 4.1
Figure 4.1
Conventional communities are based upon implicit or explicit common rules and understanding
A conventional community in the world of bricks and mortar would see the individual as being subservient to the community as a whole. Individuals would have to observe common protocols and rules of behavior and would not be expected to seek special privilege or advantage over anyone else. This also holds true in most e-mail discussion forums.
Outside of the e-mail discussion forums, an individual on the Internet is free to create their own virtual groups by establishing relationships with a number of other people. This is much like the strategy of an entrepreneur cultivating a number of key contacts, a sales person building a list of important clients or a contractor with a list of sub contractors.
This is a very different type of group from the conventional idea of a community because the individual who creates the group is effectively at the focal point of the group of contacts they establish. Yet, in the environment of the Internet this kind of group has to be treated as part of the community because of the massive connectivity.
It has to be appreciated here that the person who creates a group of personal contacts isn't the leader of that group any more than a sales person is the leader of the clients on their list of clients. They simply provide a personal concentration of communication, a local hot spot, in a vast network of interactivity.
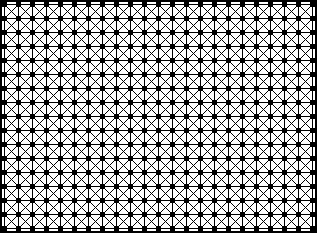
It is probable that when a person forms such a group around themselves that every person in their group of contacts has also formed a group. This would allow for everyone in a network to be both at the centre of their own group but also at the periphery of many others. In diagrammatic form, a system of interconnected self centred groups would look like figure 4.2. In this figure, everyone is at the centered of a local group of eight contacts, yet, at the same time, they are also on the peripheral of eight groups where other people are the focal point.
Figure 4.2
People can simultaneously be at the center of focus of one group, yet, through the same contacts be on the periphery of other groups where other people are the centre of focus.
An example of a hot spot of communication is the collaborative group assembled together in the virtual cafe for the purpose of this book. To the author, these are fifty people focused on his project, but, to each of the people taking part in the cafe discussions, this is just one of many different communication activities they will be party to.
The bonds, which hold these individual centred groups together, is usually information exchange. By sharing knowledge and information an individual can form strong bonds with many others, especially where he or she can provide vital or strategic information to the people they have bonded with. In return, the individual will have on hand accessibility to the knowledge of their virtual group of contacts and will be able to rely on them to cover some of their own knowledge gaps or skill weaknesses.
The advantage of the Internet environment is that contact is not limited to one-to-one conversations. Groups of personal contacts can be gathered together for discussions. The nearest simile to this situation, in the world of bricks and mortar, is dinner parties: where groups of friends or business colleagues are invited along for an evening to exchange information, views and opinions.
The virtual cafe is the on-line equivalent of a dinner party. Special guests are , invited along for a short period of discussion. Interesting guests are invited back, boring guest's are not invited again. In this way, everyone running their own virtual cafes will gradually improve the quality of their own dinner parties.
The advantage of running such discussions in the environment of the Internet is that many of them can be run simultaneously. Also, it is possible to be at more than one discussion at the same time. Imagine being able to hold different dinner parties in every room of your house and, at the same time, be present at them all.
Imagine each of your guests also being at home having dinner parties of their own with you as one of their guests, while at the same time having a discussion with your group at your dinner party. This can happen in the environment of the Internet. Is it any wonder that it takes some people such a long time to wrap their heads around the possibilities available on the Internet.
(Note: More detailed explanations of groups and cafes are contained in the second book in this trilogy "The Ultimate Game of Strategy".)
Becoming a super individual
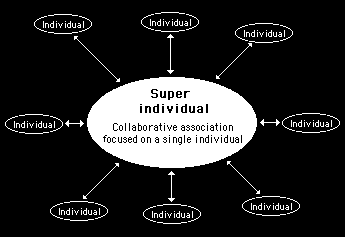
By creating a group of useful contacts around themselves, an individual will effectively become more knowledgeable, capable and aware. Through the exchange of information and through collaborative associations, they can enhance personal abilities, perhaps to the point where they become super individuals: able to vastly increase their natural capabilities. This is illustrated in figure 4.3.
Figure 4.3
Through creating a group of personal associations where there is information exchanges and implicit understandings of mutual collaboration, an individual can effectively become a super individual.
By building up a virtual community of contacts whom they are exchanging useful information and knowledge, an individual can effectively become a super individual because they can draw on the knowledge and skill sets of this personally created community. The bonding is through the mutual exchange of information, knowledge and help.
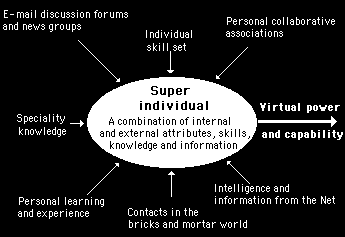
In the world of bricks and mortar, there are practical limitations to the number of contacts that can be maintained and the extent of information that can be readily accessed and exchanged. In the world of the Internet, the ease and low cost of maintaining contact with many others allows a wide variety of information and knowledge sources to be established. Figure 4.4 illustrates the make up of a typical super individual who makes full use of the Internet. Their personal power and capability are greatly enhanced through a number of different channels.
Figure 4.4
An individual can become a super individual through opening up a wide range of information sources which enhance their own abilities and knowledge
An individual, taking full advantage of the Internet to enhance their knowledge and capabilities, will effectively gain power and influence. In the world of bricks and mortar such a strategy would be treated with suspicion because nearly all associations are connected to a specific group where there is competition in a some kind of pecking order. This sees everyone, even close colleagues, as potential rivals or competitors.
In groups centred on individuals, such pecking orders do not exist. The bonding isn't about fitting into a niche in a hierarchy, it is about exchanging value. This also explains why loyalty and trust are not necessary in such groups: people bond and collaborate with each other because of the value they can give to each other.
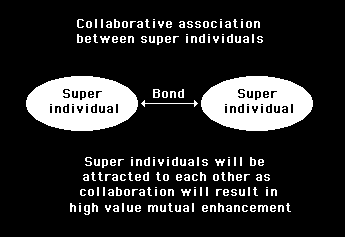
If it is assumed that everyone acts in their own best interests, people will endeavour to acquire the most knowledgeable and capable persons to be amongst their group of personal contacts. This will put the super individuals, who are making effective strategic use of the Internet, at a distinct advantage as they will be potentially more valuable as associates. The consequence would be that those who are most efficient at turning themselves into super individuals will be attracted to each other as is illustrated in figure 4.5.
Figure 4.5
Super individual will be attracted to form bonds with each other if they are each seeking to create a personal community of valuable contacts.
In hierarchical organisations, obtaining advantage by creating such a group of close associates is often treated with suspicion and even jealousy. Efforts are often made to compromise these associations or break them up.
In the environment of the Internet, rather than being resentful of others forming personal associations that enhance their knowledge and capabilities, it is strategically more sensible to encourage everyone to do this. This is because rivalry is less of an issue in the massively connected world of the Internet; it is more important that you have powerful and knowledgeable friends and associates.
For this reason, people who create cafes and strategic associations try to encourage all of their contacts to do the same. The more connected they become the more valuable will be the association.
Creating relationships on the Internet
If we take the view that the most important first step in creating an e-business is to establish a number of strategic relationships to compensate for our limited ability to know all that is needed to be known, we must devise a suitable strategy. In other words, we need to know how we can form strategic bonds with people.
In the world of bricks and mortar, a group of personal friends and contacts is often regarded as a prized possession and jealously guarded. Similarly, many people will not reveal their sources of information. Information is regarded as valuable; people will hoard it and are reluctant to share it with any but their closest associates whom they can trust not to take advantage of them.
In hierarchical organisations, many people build power bases for themselves by deliberately restricting the amount of information they give out and will conceal their contacts. Businesses are built around having carefully guarded mailing lists of potential customers.
In the world of the Internet, such attitudes are misplaced because information and contacts are forms of currency — used to fund relationships and provide the oil that keeps dynamic systems moving efficiently. This benevolent attitude towards information is common to all industries and business environments that are subject to constant and unpredictable change. People have a need to be constantly informed of new developments, changes and trends. The entertainment and fashion industries are typical. These worlds are well known for their parties and social functions which facilitate the exchange of contacts and the rapid dissemination of information.
The problem with these environments is that information and contacts are plentiful, cheap and too often unreliable. This means that the currency used to build relationships, information and contacts, has very little value unless it comes from a credible and authoritative source. The trick then, is to be seen as being credible.
Imagine yourself in a bar at a race track. You wander around, listening to conversations going on around you. It is quite likely that you'll hear several people discussing the likely outcome of the next race and there will be all kinds of different predictions as to which horse will win.
What value would you place on each of these opinions? A tipster approaches you and for a small sum of money offers to name the winner. Do you pay him to find out? Then you notice a group of people standing at the bar whom you know to be a group of trainers and jockeys. What strategy could you employ to get into conversation with them?
This scenario is a good metaphor for the situation you find on the Internet. There are countless numbers of people with ideas and information, but, because of the inherent unpredictability, the information tends to be contradictory and cancels out. The most reliable sources (even though they may not be accurate) would be from the people who are professionally involved in the activity, but, it is not easy to get into their company.
Returning to the bar at the race track, you would want to take advice and be influenced by the group of trainers and jockeys because their information would have greater credibility. But, how could you gain their respect and confidence. What could you do that would get you into their company (apart from the crass tactic of offering to buy them all a drink)?
Now imagine that you are a manager of a restaurant, and one day you recognise one of the customers as being one of the group of jockeys and trainers you saw standing at the bar at the race track. You could introduce yourself and give him some advice on the food in the restaurant and then made sure he got special service. The next time you went to the race track and saw the group of jockeys and trainers standing at the bar it is highly probable that you will be invited to join in with the group.
The trick now is to abstract the essence of this scenario and apply it to the Internet. Let's do this by isolating the main features.
1) A group is identified as having specialist knowledge which you consider to be valuable to yourself
2) At least one of the group must be able to discover that you have a specialty that is of interest to them
3) It needs only for you to make contact with one person to be privy to the conversation of the whole group
The key is that somebody must be able to discover that you have some knowledge or a specialty that interests them. But, how do you manage to do this on the Internet? How can people know about you, your fields of interest and specialty knowledge. The only way to do this in the environment of the Internet is to create a personal Web site — and then find a way of getting it "discovered" by the right kind of people.
Establishing an identity on the Web
Let's start with a green frog. This is your Web identity. It is not very efficient as a Web identity so you have to think about how you can change that green frog to give you an effective Web presence.
The first step is to turn the green frog into a computer. Next is to connect this computer to the Internet. Seems perfectly straight forward, after all there are three hundred million others who are connected, so, it must be quite easy. Right?
Here is where you encounter your first knowledge gap. You'll need to ask somebody how you get connected. They give you some algorithmic instructions which involves getting a modem and making arrangements with a company who will give you more algorithmic instructions to set up your computer so that you are connected.
Most likely, you won't have the faintest idea as to what is going on. It all seems so complicated that you'd rather not know. You are just relieved, and amazed at some point when you discover you are connected and you can send and receive e-mails and visit Web sites. Pretty soon you are so overwhelmed with the huge variety of different information you are exposed to that you forget all about that initial first step you took in becoming connected.
As a casual user of the Internet it may not concern you very much how you are connected. You have a direct connection to another computer (your ISP — Internet Service Provider) linked directly or indirectly to the whole of the network. It works fine, so there is no need to go into details as to how it all happens.. However, as a professional user, someone who is going to use the Internet as part of their professional business life, it may be prudent to take the trouble to look more closely at what is happening.
For starters, the initial connection you made was probably opportunistic. A decision made in ignorance. Was it the best choice you could have made? How easily can you change if you realise there is a better choice elsewhere? What if you wanted to change? Your e-mail address is likely to be valid only while you are using your current ISP.
In a world of constant change, flexibility is vital. If your ISP goes down or becomes slow because it is trying to handle too much traffic you are handicapped. What insurance have you got that your ISP won't suddenly go out of business. If you change your ISP you lose your e-mail address and will have to notify everyone you know. You'll have to resubscribe to e-mail discussion forums, change the details on many Web sites that recognise you through your e-mail address. If only you'd known a little more when you connected to the Internet, you could have saved yourself all these potential problems.
By appreciating that you have knowledge gaps, you can take precautions. In the first place you can think of your first connection as simply a temporary expedient to get on to the Internet to be able to get enough information to connect more efficiently.
There are thousands of Web sites that will give you information, but, it is likely to be thoroughly confusing. The best way is to find some e-mail discussion forums to join and ask questions. Strike up on-line acquaintanceship with knowledgeable people and ask their opinions. It is essential that you ask several people because everyone has knowledge gaps and you'd have no way of knowing whether you were getting the right advice unless you could make comparisons.
In my own case, I was very slow at understanding what the Internet was really about. I had a vague mental model as to how it all worked and this had served me faithfully for years. But, as I contemplated the possibilities of being involved in an e-business situation I became consciously aware of many limitations.
It was a chance e-mail discussion I had with a contact in Canada that first opened my eyes. This contact, Yvan Caron, was investigating the commercial possibilities of P2P (person to person) file transference. He sent me an e-mail enthusing excitedly about the business opportunities it opened up. His e-mail contained so many terms I was unfamiliar with that I couldn't understand what he was talking about.
I confessed my ignorance and he went to a great deal of trouble to explain how the transference was organised. I didn't follow all the technicalities, but it was enough to totally change my conception of how the Internet worked. It provided me with a new insight and at the same time made me acutely aware that for years I'd been using the Internet without really understanding how it worked.
As I understood from Yvan Caron's e-mails, the Internet isn't about computers talking to each other, it is about applications talking to each other. This may be obvious, but, it is such simple changes in emphasis that can lead to greater understanding. As he explained, application programs send each other messages and listen out for messages being sent to them.
The problem, however, was that although Yvan's explanation had given me a valuable new insight, it had totally destroyed the mental image I had built up over the years. I now had to start from scratch to create a new model.
I was reluctant to start going into much technical detail because it is so easy to get sucked into weeks of hard study. I wanted to stay away from the detail and work with broad concepts; this might not make me technically competent, but, at least I might be able to see through the fog.
In trying to form a new mental model of how the Internet works, I discovered many different kinds of knowledge gaps. Try as I might, I couldn't get a complete picture into my head. Fortunately, I belonged to a very techy e-mail discussion forum (www.evolt.org) where many Internet gurus and Web site designers hang out. To this forum, I sent the following post:
I'm trying to figure out a neat mental model to explain how the Internet works without having to involve any technical detail. I thought I had a good idea as to what goes on under the hood until I tried to write down a simple explanation. The more I try, the more knowledge gaps I discover.
Starting from the beginning, I make a connection to my ISP. I guess some application does this by making a telephone connection and in computer speak identifies itself and presents an appropriate password. The ISP then allocates my computer a temporary IP address.
Presumably, the ISP then listens out for any messages for this temporary address and passes them straight on to me. If I send out messages where do they go? Does the ISP computer simply pass them on, adding my temporary IP address? If it passes them on, where does it pass them on to? How do they get to a destination I want them to go to: 1) when I send someone an e-mail; 2) when I specify a link with my browser?
Once I'm connected, does my ISP computer keep listening to my connection to see if I am sending any messages? How does my ISP computer detect the messages that are being sent to me? Are these messages being routed directly to it or is it just listening to all messages on the Internet and selecting those that apply to its own clients?
It's a very hazy picture I have. Every time I think I'm beginning to understand, I get stumped with another knowledge gap.
I'd be grateful for a little light...
peter
http//:www.petersmall.net
There were three responses. The first from Anthony Baratta, President of KeyBoard Jockeys, he described how the initial contact was a shout to your ISP to give you an identity (a temporary IP address). Your application then sends this identity in a short message to a universal database that is constantly recording who is currently on the Web and where they are (the database can tell where you are by the route the message takes through different computers to reach it).
A mystery had been cleared up. I had always wondered how messages found their way around the Internet. The answer was so elegantly simple: you created an identity when you log on and this identity is placed on a map that resides in a computer that every other computer has access to. If an application wants to send a message to somebody, it just routes it through the computer that has the map.
(Note: the map is in fact duplicated on many computers around the Internet. These computers are in constant communication with each other, exchanging updated information at least every thirty seconds. Each collects information about computers in their own locality: to know which are currently connected, their identity and where they are located. This information is then passed on to all the other computers holding a "map", so within a few minutes of logging on, every computer in the world knows how to find you.
The second response was from one of the people in the virtual cafe, Scott Dexter, from California. He is also one of the more active members of evolt.org and is involved in the construction and content of the www.evolt.org Web site. He explained the Internet in terms of a metaphor of the cafe, explaining how messages get passed from one computer to another as they pass from the sender to the receiver.
He explained how messages get sent with a lot of extra information (in a header), which is read by all the computers that handle the messages. This information includes the name of the sender, the time it was sent and the name of the intended recipient. It is this information that enables computers to know if a message is for them, or, if not, to know where to pass the message on so that is gets nearer to the intended recipient.
The third response came from Miraz Jordan, who runs Internet education courses in New Zealand. Besides directing me to his own lecture notes on the Web, he pointed me to a very authoritative Web site (www.livinginternet.com) that explained the Internet in a reasonably non technical manner. Although it contained a great number of pages of detailed information, by spending a whole day on this site, I found most of my knowledge gaps closing and I was at last able to construct a new mental model of how I understood the Internet to work.
A mental model of the Internet
The most important change in the way I started to view the Internet was that I ceased to imagine it like some form of telephone network where computers connected to each other in order to communicate. I'd always viewed the Internet as a complex arrangement of wires and switching mechanisms. I was shocked to find it wasn't like this at at. In its place I now had a "name space", where the names were like islands in a vast ocean of water with no connection between them other than the currents in the water.
For these islands to communicate, they had to break all their messages up into bits, put each bit in a bottle and throw the bottles into the ocean to let the currents take them to their destination. This was the key break through. It wasn't about making connections with other computers: the moment a message or any part of a message is sent it becomes stateless and the sender loses all contact with it and there is no contact at all with the intended recipient or any of the computers through which the messages are passed.
Note: The way these stateless messages get passed around from computer to computer on their way to their destinations is both ingenious and remarkably simple. To limit the effect of a breakdown the messages are all sent as small data packets (about 1,000 characters long i.e., 1 kilobyte). All the data packets are sent to a main highway (the backbone of the Internet). This consists a number of heavy duty computers — known as routers — that pass all Internet messages between then.
They each carry continuously updated maps of the Internet that tell them the location of every computer currently on line. This allows them to be able to work out the best way to send the packets to be able to reach their destination. However they don't just send a packet the physically shortest route, they try to send it in the shortest time which might mean routing it around heavily congested parts of the Internet.
Each data packet, passing through a router, contains a record of its travels through the network together with the times at which it reached each computer it passes through. This allows routers to work out all the current transmission speeds throughout the entire network and calculate the probable fastest routes to pass the packets on towards their destinations. Routers pass these data packets to each other until they reach the locality of the destination computer. Then it is passed into a local network to be passed on to the computer the packet is addressed to. This destination computer will wait until all the packets of a particular message arrive and then put them all together to recreate the original message as it was sent by the sender.
Routers are constantly communicating with each other, updating each other about maps and transmission speeds, working as a kind of team to ensure all packets of data get to their destination in the shortest time possible. They correspond with each other every three to 30 seconds and if a communication goes over the thirty second limit the receiving router assumes the late sender is out of action and tells all the other routers to route messages around it.
Once it dawns upon you that all data packets and messages are stateless — quite isolated and independent of sender and receiver while they are in transit — you can look at the environment of the Internet in a completely different way. Not only are the data packets and messages stateless, so are the senders and receivers
A sender can pop up anywhere on the Internet to send a message. It doesn't matter where they are physically located. Similarly with receivers, they can change their position in this name space at any time and still receive messages that are addressed to them. This can give rise to a phenomenon that it impossible to create in the world of bricks and mortar, a virtual entity.
Virtual entities
A virtual entity is an entity that has no fixed form or shape. It is created out of components that are connected together only by the imagination. Such things are impossible in the physical world. Imagine creating a perfect partner for yourself, choosing all the best features and body parts from a host of film and television personalities and putting them all together to create the perfect person. Imagine being able to give this virtual partner the personality of the nicest person you know and the intelligence of the cleverest.
### End of chapter 4 ###
Back to indexNote: This book lead to the creation of the stigmergicsystems.com website |
Copyright 2000 - Peter Small
Peter Small <peter@genps.demon.co.uk
All rights reserved by Pearson Education (Longman, Addison-Wesley,Prentice Hall, Financial Times for FT.COM imprint